My take on SOA,Oracle BPEL, ESB, OSB, BPM,iPaas, cloud computing, AWS ,MEAN stack.
Friday, May 10, 2013
OAuth Security implementation in OSB/SOA (REST/SOAP) service
Wednesday, February 3, 2010
how to address security concerns : OWSM –do we really need it??
Security is a major factor to consider when you are designing a system. It depends on a lot of factors like the systems involved in integration, the type of information, the mode used for exchange of data etc. There will be lot of handshakes within the organization and with outside entities. Every client will have their own security measures and standards in place which has to be met before they will allow the integrations to be in production. So getting security clearances is a major roadblock (necessary evil) in all projects. So always make sure addressing security concerns becomes part of your design process.
Security is a vast topic and to define security we will need to know what all concepts it deals with. I have listed the core points that constitute security.
• Authentication: an act of establishing or confirming something as authentic, that is, that claims made by or about the subject are true
• Authorization: is the function of specifying access rights to resources
• Integrity: has to do with perceived consistency of actions, values, methods, measures, principles, expectations and outcome.
• Confidentiality: is ensuring that information is accessible only to those authorized to have access" and is one of the cornerstones of information security.
• Non-Repudiation: is the concept of ensuring that a party in a dispute cannot refute the validity of a statement or contract.
In today’s world where the users /systems are spread across the globe and communications happen over internet there are high chances that any of the above factors may be compromised. We will see the different methods that are being currently used for securing the data transfer between systems.
I will mention the most widely used methods
· Transport Level Security -- TLS/SSL/VPN/ HTTPS (The most widely used)
· Message Level Security --WS-Security (Open Standard)
Transport Level Security
The SSL/TLS VPN gateway often authenticates the client. If the client does not have a digital certificate, the VPN gateway may send the client a request for other authenticating information—usually a username and password. When the client responds, the SSL/TLS VPN gateway checks if the authenticating information is correct. A virtual private network (VPN) provides a secure communications mechanism for data and other information transmitted between two endpoints.
- Transport-level security (e.g. HTTPS) is a point-to-point security model where the channel is protected between two parties. However, many times the service consumer and service provider are separated by intermediaries (e.g. an Enterprise Service Bus).
- SSL/TLS VPN gateway authentication often is vendor-specific. So are most other aspects of SSL/TLS gateway operation.
Message Level Security
In situations where the service consumer and service provider are separated by intermediaries, message-level security can provide an end-to-end security solution. The secret is that with message-level security, you can encrypt the message using the public key of the final destination. In this way, only the intended receiver can decrypt the message.
Web Services Security (WS-Security) is an OASIS standard to describe how to implement message-level security with Web services. Specifically, WS-Security describes how you can add confidentiality (e.g. encryption), integrity (e.g. digital signatures), and authentication (e.g. username and password) to a SOAP message. In most cases, XML encryption and XML signatures are the mechanisms for securing the message.
- Message level security secures the message content itself, but it does not secure the communication channel.
- To apply message security, you have to make several configurations on both the client side and the server side.
So when you build integrations you will need to accommodate either message level or transport level security to the messages send across to different systems.
This is where OWSM comes to our help. It is one place where we can configure the security features that you want to incorporate whether its message level or transport level. This tool acts a gateway to incoming and outgoing messages .We can setup policies where message can be decrypted in request pipeline and encrypted in response pipeline.
I am listing down interesting factors which will make it an attractive option for solving your security issues.
• OWSM is a proxy that runs in the App Server
• Accepts or rejects incoming requests like a firewall
• Transport protocol translation
- Incoming: HTTP(S), JMS, MQ
- Outgoing: HTTP(S), JMS, MQ, or a custom protocol
• Supports both SOAP and standard XML messages
• Content Routing
• Policy - Set of operational tasks that are performed at a Policy Enforcement Point
• A Policy is separated into
– Request Pipeline – A set of policy steps that are executed during the processing of a Web Service request.
– Response Pipeline – A set of policy steps that are executed during the processing of a response to a Web service request
This makes the integration process independent of any security related programming. OWSM will act as a centralized server for managing all your security concerns. Thumbs up from me J
Thursday, July 17, 2008
how to call secured webservices from bpel
to start of with refer the blog by Marc Kelderman on calling basic secured webservices
You can add these properties from partnerlink also.
Click on the partner link which invokes the secured webservice wsdl. Select the properties tab . Click on create property and add the 3 properties and corresponding values
wsseHeaders
wsseUsername
wssePasswordThe header value must be credentials
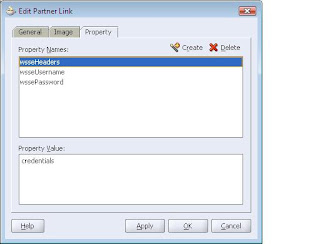
The sample partner link entries in bpel.xml will look like the following
<partnerLinkBinding name="HelloWorldService">
<property name="wsdlLocation">HelloWorldService.wsdl</property>
<property name="wsseHeaders">credentials</property>
<property name="wsseUsername">geo</property>
<property name="wssePassword">secret</property>
</partnerLinkBinding>